攻防世界-crypto
攻防世界-Crypto
[简单] 初识RSA
刚开始还以为qp,pq跟dp,dq一样
后来发现题目给出了
pq = p*(q-1)
qp = q*(p-1)
hidden key
1 | import random |
easychallenge
这里我把题目给出的pyc文件重命名为test.pyc,反编译后的源代码放入test.py中,无需事先创建test.py,直接在pyc文件所在位置打开终端,输入下面这句命令即可:
(我用的是MacBook)
uncompyle6 -o test.py test.pyc
简单的LFSR
matrix()
矩阵所处环的表示
ZZ:整数环
QQ:有理数环
Zmod(p):p为素数,定义在Zp上
矩阵操作
声明
超完整定义
mt = matrix(QQ, 3, 2, [1, 2, 3, 4, 5, 6])
完整定义
mt = matrix(ZZ, 3, 4) #定义一个在整数环上的3行4列的矩阵
mt = matrix(ZZ, 0, 4) #定义一个在整数环上0行4列的矩阵,后期可动态添加行
部分定义
1 | mt = matrix(QQ, 3, [1, 2, 3, 4, 5, 6]) #定义在有理数环上的3列矩阵,并赋值 |
求矩阵X满足XA=B
X = A.solve_left(B)
求矩阵X满足AX=B
X = A.solve_right(B)
确实不会直接看的WP
题目源码:
1 |
|
分析一下题目逻辑。初始化数组 initState ,即为LFSR(线性反馈移位寄存器)的初始状态,mask 是flag转二进制之后的数组。
最主要的操作就是进行256轮LFSR计算
lfsr函数逻辑不算复杂,输入两个长度为128数组state, mask,输出output值为$out=\sum{state_i \times mask_i}$- 注意到每轮
state数组取值会向右移动一个位置,同时initState长度会增长1,即数组尾部追加了output值
关键的关系式$out=\sum{state_i \times mask_i}$
可改写为矩阵乘法形式$out=State \times Mask$
State是 $1\times128$ 向量,Mask是 $128 \times 1$ 向量
256轮循环最终输出 initState 数组后256个元素,命名为 outputState,其中$outputState_{0…127} \times Mask = outputState_{128}
outputState_{1…128} \times Mask = outputState_{129}
\cdots
outputState_{127…254} \times Mask = outputState_{255}$
接下来就是简单的线性方程组求解了。
最终exp:
1 | #sage |
rsarsa
sage脚本
1 | p1= 1687218514918517855575434101578033845149036490224579822827979075465068557041497711556817903 |
告诉你个秘密
积累一下经验吧,这种东西一般就是混合加密了,虽然意义不大,但是记下密码特点终归是不错的
1 | 636A56355279427363446C4A49454A7154534230526D684356445A31614342354E326C4B4946467A5769426961453067 |
这个容易看出,数字字母,大概就是base
解出来后
1 | cjV5RyBscDlJIEJqTSB0RmhCVDZ1aCB5N2lKIFFzWiBiaE0g |
base64
1 | r5yG lp9I BjM tFhBT6uh y7iJ QsZ bhM |
键盘密码
你猜猜
内容
1 | 504B03040A0001080000626D0A49F4B5091F1E0000001200000008000000666C61672E7478746C9F170D35D0A45826A03E161FB96870EDDFC7C89A11862F9199B4CD78E7504B01023F000A0001080000626D0A49F4B5091F1E00000012000000080024000000000000002000000000000000666C61672E7478740A0020000000000001001800AF150210CAF2D1015CAEAA05CAF2D1015CAEAA05CAF2D101504B050600000000010001005A000000440000000000 |
504B0304是zip文件头
要在winhex中创建新的文件1.zip
放到ARCHPR
1 | daczcasdqwdcsdzasd |
flag_in_your_hand1
之能说是积累经验吧
代码审计js.文件
1 | function checkToken(s) { |
以为输入这个就能过了,但没想到不行,看WP说找ic
1 | function ck(s) { |
也就是这个,变为字符应该就是token了

竟然错了

问题在这if (a[i] - s.charCodeAt(i) != 3)
我们要让输入的字符ASCII码与元组a中数字相减等于3

这个就可以了
工业协议分析2
题目暗示说flag在异常流量中,那直接明文匹配查找flag,没有换成16进制查找
注意要选择分组字节流 字符串 

将右下角的16进制转字符即可

点as Printable复制
sherlock
刚开始就觉得有些大写字母很奇怪,还真是要收集大写字母
1 | 直接cat 1.txt | grep -o [A-Z] |

1 | cat 1.txt | grep -o [A-Z] |tr -d '\n' |
可以删除换行符
grep -o 只显示匹配到的字符串
tr -d 删除指定字符
1 | ZEROONEZEROZEROZEROZEROONEZEROZEROONEZEROZEROONEZEROZEROONEZEROONEZEROONEZEROONEZEROZEROZEROONEZEROONEZEROZEROONEONEZEROONEZEROZEROZEROZEROONEONEZEROONEZEROONEZEROONEZEROZEROZEROONEZEROZEROZEROONEONEZEROZEROONEONEONEONEZEROONEONEZEROONEONEZEROONEZEROZEROZEROZEROZEROONEONEZEROZEROZEROONEZEROONEONEZEROZEROONEZEROZEROZEROZEROONEONEZEROZEROONEONEZEROONEZEROONEONEONEONEONEZEROZEROONEONEZEROZEROZEROONEZEROONEONEZEROONEONEONEZEROZEROONEZEROONEONEONEONEONEZEROONEONEONEZEROZEROZEROZEROZEROONEONEZEROONEONEZEROZEROZEROZEROONEONEZEROONEZEROZEROZEROZEROONEONEZEROZEROZEROONEZEROONEONEZEROONEONEONEZEROZEROONEZEROONEONEONEONEONEZEROZEROONEONEZEROONEZEROONEZEROZEROONEONEZEROZEROZEROONEZEROZEROONEONEZEROONEONEONEZEROZEROONEONEZEROZEROONEONEZEROONEONEONEONEONEZEROONE |
接下来又两个思路,一个是二进制一个是摩斯电码
文章内容是福尔摩斯所以先试摩斯电码,但摩斯电码要有空格…
还是先试二进制
1 | # 开发时间:2023/2/26 15:53 |
safer-than-rot13

词频分析网站https://quipqiup.com/
要小写补上_

cr4-poor-rsa
读取公钥脚本
公钥中有 e,n读取出来
1 | from Crypto.PublicKey import RSA |
因为这里c是未知的,而flag.b64又不知道怎么打开,
好吧原来是代码写错了,是可以解开的
1 | import gmpy2 |
crypto垃圾邮件
还真有垃圾邮件解密网站
cat’s gift
莱布尼兹π的莱布尼兹公式。

欧拉研究出的

根据脚本算出的
1 | def gift(n=100): |
就是π了
找个谐音还是事物的英语
pie
二元一次方程
还是第一次用python解一元二次方程
1 | from sympy import symbols, solve |
1 | import libnum |
babyFibo
已知c,s c = m^s
可以通过再次异或得到m
1 | import libnum |
1 | #b'8OcTbAfL6/kOMQnC9v8SNmmSzvQMeGTT8vANM1T+7vIce2fo0fc2RnScrNxTSmeSyuMjMF//w8BWaXX91dsGcnvmreg0NQTw96ceVVXj3sQ3Znn51OU1S0bOyaMtNHTj36AcWFqewN4zRUXD6agGbAPE+tQtd3XG0doAa1Ll9fhcQ1zk0McTM1bv8PIQOAnn3vQ3UgLD3PsONXLs4KkXMnjTyMEQOFn/0uYVUwOY1PsleEHCyNopRVDr+Kc0e2PH9v0XNXfprfIPU3nw7KYTNX/G7twLSkHoyaUlQHXi3v02UHmdy/4iNgme3Pc8bgPp+tYWV1+YzPkXYkXM4ulUc27DrM4SNUPT2fQlckj1qP4Fal+YoPYJMlyZ8qhXfF3Y0tUDdUXl3vg0dFTi++VVOFfH/dgMS1ru9N8WU0HF9cUCTgPe+qVdSn/u7Mkda0GTw/QDcWPZ9KYGN2jSzfk0OVrMzt0yRHD64KMrUgPF2sFWcmP56KZSTAD61PUGeXrd49MgU1bL8OsVNWj91vIsalXwqf0qaWbwzv0lWETA4eElS3L99cYmU1nv9dRQTWbDyclScQTN6NIhV2j//+ZWbH7Z68kwM3Dy4dcUc1PQy8kRTl/4zcU9WGWfoakOMXuf69MXZQTEz+kJT1Dar8UN' |
Xor很心疼你
1 | # b'8OcTbAfL6/kOMQnC9v8SNmmSzvQMeGTT8vANM1T+7vIce2fo0fc2RnScrNxTSmeSyuMjMF//w8BWaXX91dsGcnvmreg0NQTw96ceVVXj3sQ3Znn51OU1S0bOyaMtNHTj36AcWFqewN4zRUXD6agGbAPE+tQtd3XG0doAa1Ll9fhcQ1zk0McTM1bv8PIQOAnn3vQ3UgLD3PsONXLs4KkXMnjTyMEQOFn/0uYVUwOY1PsleEHCyNopRVDr+Kc0e2PH9v0XNXfprfIPU3nw7KYTNX/G7twLSkHoyaUlQHXi3v02UHmdy/4iNgme3Pc8bgPp+tYWV1+YzPkXYkXM4ulUc27DrM4SNUPT2fQlckj1qP4Fal+YoPYJMlyZ8qhXfF3Y0tUDdUXl3vg0dFTi++VVOFfH/dgMS1ru9N8WU0HF9cUCTgPe+qVdSn/u7Mkda0GTw/QDcWPZ9KYGN2jSzfk0OVrMzt0yRHD64KMrUgPF2sFWcmP56KZSTAD61PUGeXrd49MgU1bL8OsVNWj91vIsalXwqf0qaWbwzv0lWETA4eElS3L99cYmU1nv9dRQTWbDyclScQTN6NIhV2j//+ZWbH7Z68kwM3Dy4dcUc1PQy8kRTl/4zcU9WGWfoakOMXuf69MXZQTEz+kJT1Dar8UN' |
1 | 解题.py |
直接找的WP
核心部分在我看是这里
1 | for r in range(2,251): |
通过爆破的方式,求出r,key,与flag所在位置,因为加密代码中虽然有两个循环,但是他最终是有一个确定的r与key值的
[中等偏下] 线性反馈移位寄存器
这个与之前那个LFSR类似,但是还是不会做,且看WP
原文链接:https://blog.csdn.net/figfig55/article/details/128632051
1 | from secret import secret |



1 | #sage |
转轮机加密
托马斯·杰斐逊- 轮转密码题
拿的别人的脚本稍微改了一下.
1 | # 开发时间:2023/3/12 8:52 |
best_rsa
共模攻击-扩展欧几里得算法
1 | import gmpy2 |
RSA_gcd
1 | p=gmpy2.gcd(n1,n2) |
shanghai
维吉利亚密码
OldDriver
低加密指数广播攻击
1 | import gmpy2 |
easychallenge

1 | # uncompyle6 version 3.9.0 |
Decrypt-the-Message
Poem Codes
Poem Code 最显著的特点就是一首诗歌。
加密过程
给出一首诗歌
for my purpose holds to sail beyond the sunset, and the baths of all the western stars until I die.
给出5个关键单词。
“for”, “sail”, “all”, “stars”, “die.”
对其进行拆散:
f o r s a i l a l l s t a r s d i e
接下来按照 字母表顺序 进行编号,若遇相同字母,则继续 +1
| f | o | r | s | a | i | l | a |
|---|---|---|---|---|---|---|---|
| 6 | 12 | 13 | 15 | 1 | 7 | 9 | 2 |
| l | l | s | t | a | r | s | d |
| 10 | 11 | 16 | 18 | 3 | 14 | 17 | 4 |
| i | e | ||||||
| 8 | 5 |
We have run out of cigars, situation desperate。
先对对其进行编码。因为给出的5个关键词,其长度为18.所以以18为一组。
若一组长度不满18,则用abc(不要求有序)进行补充。
将排好的消息,按照之前给出的诗歌字母编号写下密文。
for my purpose holds to sail beyond the sunset, and the baths of all the western stars until I die.
如, for --> eud tdk oek 那么得到的又可以按照5个(适当个数)为一组进行重新分组,得到最后密文。
————————————————
版权声明:本文为CSDN博主「J1ay」的原创文章,遵循CC 4.0 BY-SA版权协议,转载请附上原文出处链接及本声明。
原文链接:https://blog.csdn.net/weixin_45530599/article/details/108027293
审题解题
首先我们得到一首诗歌
1 | The life that I have |
以及 decrypted message (解密消息)
1 | emzcf sebt yuwi ytrr ortl rbon aluo konf ihye cyog rowh prhj feom ihos perp twnb tpak heoc yaui usoa irtd tnlu ntke onds goym hmpq |
解题脚本
已知原理,我们可以运用网上大佬的 解密工具 ,:
1 | python poem.py poem msg |

ecb,_it’s_easy_as_123
只有一个cry300放到winhex里面看看
504B0304是zip文件头
解压得到ecb.bmp和task.txt
BMP文件实际上不是有效的图像文件,因为它是加密的。它的前几个字节很有趣:加salt __前缀表示此文件OpenSSL加密的OpenSSL解码。紧接着8个字节(Ab31b5e5ca 3db94d)是用于加密文件的salt 。文件的其余部分是加密数据。
原因分析:
因为标题和任务描述中有一些提示:ECB-ECB加密对于图像来说是出了名的不好,因为相同的明文块产生相同的密文。4K分辨率-这告诉我们图像要么是3840×2160像素,要么是4096×2160像素。黑白-我们很可能会看到很多只有白色的积木。
所以,考虑到这一点,让我们来看看十六进制转储:
1 |
|
查阅wp后才发现,只需要改动文件头128位即可
脚本如下
1 | # 开发时间:2023/3/12 13:25 |
还有一个更好的解决方案。我们只需删除前16个字节(Salted__和Salt),然后用有效的BMP报头替换密文中的前几个字节。这是可行的,因为BMP存储原始数据,我们不会得到无效的块。
1 | Bash$xxd sample.bmp|head-n 8 0000000:424d 7648 3f00 0000 0000 7600 |
enc
解到
ALEXCTFTH15O1SO5UP3RO5ECR3TOTXT就不会了
要改为这种形式
ALEXCTF{TH15_1S_5UP3R_5ECR3T_TXT}
wtc_rsa_bbq
读出两个文件信息后,还要再次读取信息内容
1 | # 开发时间:2023/3/12 15:01 |
使用工具RSACTFTool进行分解,将key.pem与cipher.bin移到与RsaCtfTool.py同目录下:
1 | sudo python3 RsaCtfTool.py --publickey key.pem --uncipherfile cipher.bin --attack fermat |
工业协议分析1
找到最长的一条
1 | data = "iVBORw0KGgoAAAANSUhEUgAAAdAAAABiCAYAAADgKILKAAAAAXNSR0IArs4c6QAAAARnQU1BAACxjwv8YQUAAAAJcEhZcwAADsMAAA7DAcdvqGQAABzXSURBVHhe7Z2Js11Fncfn75maqZmaqZkaS0elXAp1GHRUhGFAQHYQFQRFBWQRiBoBWQyyKaBsxo0tCAgkQHayQEL2jSxAyEoSIAHOvM/JPTPn9fv1Od19+9z3bvh+qr5FkXe77z33ntO/7l//fr/+m0IIIYQQ0ciACiGEEAnIgAohhBAJyIAKIYQQCciACiGEEAnIgAohhBAJyIAKIYQQCciACiGEEAnIgAohhBAJyIAKIYQQCciACiGEEAnIgAohhBAJyIAKIYQQCciACiGEEAnIgAohhBAJyIAKIYQQCciACiGEEAnIgAohhBAJyIAKIYQQCciACiGEEAnIgAohhBAJyIAKIYQQCciACiGEEAnIgAohhBAJyIAKIYQQCciACiGEEAnIgAohhBAJyIAKIYQQCciACiGEEAl0ZkDff78oNm/ZV8xfuK2Y8fxrxex5W4vlK3cVe/Ye6L1CCCGEGF6yGtC33n63uOPuNcW/fHJG8bcffsarf/3UjNLAVtz/h/Xm6/h3IYQQYiKSzYBufePt4thT55qG0NXxp8/ttTqIDGj/vP3Oe+VKf/L1y4qTzppffOq/ni/+6bDpxY+ve7n3irHw/VrKzdsjE6tFL24v7p26rrhs0pLy8x3+pZnFhz/zbDnZ+th/PFd86auzi3MuWFhcc+Py4qFpG4s1694cNcmKYf/+94oXFm4rbr1zdXHe9xcVn/+fWcVHPvv/7/WVk+YU371kcXHbyN9nzd1a7JVXRHxAeGdknFi2Ylfx+FNbiql/3lA8MPK8/+XJzcXLy3eWz80wcdxpc4t//sSMciw55Zz5xXW/WF4+zwcODO46shhQBqCjvzbHNIKWfnjVS72WB2HQtl7XxWB+KDJz9tbiM1+eaX6HTQbUej3KxZKXdxRXTV5aehys92kThm/u/Dd6vbXD9sDd960tPvH558z+fGKicfmPl5RGW4hBsnDx9lGT10q5YTuNyemHDn/WfAYQk8xf3LqyeGPb271W3bLl1X2l0bP01PRXe6/ygwG1ruOLx88uFr+0o/eqbsliQPlhrAvxiZVBHW4Y63Vd3EiHGtOe2Gx+d5XGw4CuWLWrOPv8BWbfsXp25uu9XptZMDIQ+SYRoXrksU293oToFp6Rc7+3yLwPUS7ee+/94r6p64t//Ph0830sYWSffGZLr4duwLt0wcWLzfdHGNE2fAYU/f1HpxezR1ajXdO3Ad24aW/xdx+xL+LIY2cV0597rdj95v7yh9y9e3/pysOFUEcGNA1mcKyerO/us0fNLF2iv/vjht6rx2K1Q6ngAvrlHau890OKdu3a3+vdz2NPbs7ynq++tq/XoxDd8MrGvaUHzrr/6srBu+++X1w5eanZf4gwvF2BXbDes1KIAWXhdta3FxSHHWl7nNiueXNP+/jRD30b0Ft+tcr88J/7ysxi+/YwV4AMaBpTbls55js75uQ5xcpVu3uvaMZtWymFnbveKc449wWzv1SxV9rG3BfeyGI8+d6E6IrXt75VDvisjKz7z1UOMEJW3zF68un8K9E9ew6U+5bW+1UKMaAVrGbJ9vj0F58f088fH3ql96pu6NuAEvzhfmjEDCMUGdA08PXXv69/+Nj0cq8jlHrbumLZsfOdoD3wE8+cV9zzwLrS3cpqjz1LghrwUODJwBiyh0lAAK8norsJ2n3yC2Mfmkpfv2BBOQDQ9959B8pgph073iknGLi+L5+05P/2Z2+/a/S2ghA52LV7f3Hrr1eXwS7u/dmkfmla4bG4mfqnDaU3kBiDm+9YVfzbp+3Px/OBpysnN94yduLvKsaAVry4ZMeYfggi7JK+DCgrTPcDo3//3LNRkVAyoPGQMuR+X0SWxuC2rxQDRunkrx80eD5d+MPFwaviig0b9xSbNu/t/Z/NXfesNd+P/Z6/PtMehAAYcaIRyVEWIjd4Uax7tE39wGTRWo0hDIqVi8/E252QVyJyPhfs/YZ4jFIMKBBhX++HbIQu6cuAWhYfff/yF3uvCEMGNB5r8tK2YnNx21eK4Wc3LDP7QAQjPPNsuCciBvbUfYMEq0shJgKkSln36FfPmFemWvk8eP1wz+/WmX1iXDCuPja8sse7Ul67vv8IdfZk8ULV+/3a2fPNgMNUA0o0fb0fvHJd0pcBfXrGq6M+bCVcFjHIgMaDa8j9vnhwYnDbVwpl/oJtZnvExv7qtXGrzhhWrdltvu9RJ85Jzh8VIjdLl+0cdX/iPmVbgQkg5DagBPL5tjVw2bbx69+uMdv+fMqK3ivSYT/S7Ze8zRMco4pSDShZB/V+cEF3SV8G9M+PbBz1YSs1RX5ayIDGw2zO/b64+WNw21cK4cDI+2OsrPa4UEnM7hLC7K33nnL7qt4rhBh/eE7JSybHkqIFbHnUyW1AMUhWf6d/64XeK5ohnoFVm9uez99PoQVyS90cVAwnk13yvev/jlINKC7qej9HHD2r95du6MuAYijrH7ZSbOSTDGgargvzhl/GzRLrbesKgT1Gqy2i4lDXsG9pvTdBSkJMJJ6f/bo3HSu3AaVwidXfE0+FR9N+77IXzT4I/kvFSt2ZOedgnqaVhpJqQL98wujv89RvhE0cUunLgPoM33gaUGY0zHZwV7BKeXBklcznmfb45jLijIiyrlx89EvEJxFwvx8Z4Pn8vO9LS3eU0aa5YVZZ/75+ct2y3l/CqLetKwRfcASBCIMoCeYzoKkP3kSHqGXuK6InmaCwz4sbO/Re5jdZ8vLO8n4kv4/VEFswg8h95d4nXuLhaZvKz86zwUqJKOpQSAOhqMYfHnyl7IPnmmozuZ8rVmDsTfL9Mm48+OjG8n2pUoXXJTc5DShuYcsYEbQTkk9dQUERtw/0q9/EebgqGHfdvtj7rO5dKwI45TmmPzcv/uIfja56l5soA9qW/Nqm8y+yQ4r7NaC4SbjpybOigIDVV124DNgvzJVki1uGh833MCDqvhIuTjGJihtuXjHmdTGRtKRh1Nte/TN/1SGLetu62li3/k2zHaKowSDwrYBx2XQx0HXBFT8Zu1pwXdBMBM88z1/VicCQ52b5qzVhELjvcMFZ7REFN2Jd7gScWH3VB2qiPUkP8r03rn6eWT6jBQMi1WRO+6Y/v5iI/7vvXVtGpaeC4SHYrS2PGRckv9mCRduCJy5t5DSg6zfYvwmBOzGsWWs/39wnsfC7UFDH7Yu8zQqrGEyKASUX3e2HMbZLht6AMpD6wq/bxN5ETK1VC2bW1g3iEwnEhHKDVSWEKLJQ3A1zSoPFUG9bVxusAKx2zCT37UsfyGJoMuKscIYBCv+7n33StQcnQUwKb7q1PV+uEgNFFZhSwRGCHz8irC4wq5SY2AVWrlY/m7YcTD1atXp3OZmxXuOKZ8KtQ0x97ZCKPZX++5S55So1ltdef2uMJydE/Y4bFTkNqC+oM9aI4K2wCj6wCIidODCBcvv5xncWjurH/TtKMaBECrv9dL2lM/QGlFJOVttQMXBwXSlwikFoZZG6uBEp6fUdoxYkM/JQfvrz0QMwq5EY6m3raoOZqNXu0qvz5Yu1wQPomzjxm3RRQSU37Fm7n52cWa4NQ+r+rU31IDK2L1IqNBEYGML2HWNn+4h8WlYw3OPW330iX68qYk6lGlx81uuahDGKcQuTZ+xLhWoSK6amdJAYchpQ0tisvnCdx+LuJVaKKTS/bmRF7AYk4XVg7KtT/3ulFAPKqtbthzG6S4begOI6tdoiaiFWx3pZf69E7pP7o7bhm+2FigHCzYlClEYMxR2Aud4Y6m3ragL3qC9X7NHHB1uMnYHB+hyVmGCQ7jNR4VAF9zMT9MD+nvvvIcJgYrzwiqRM7JA1wFlg5Kz2jBExHpm6LrnypXIVzThh/T1E1Qq+DfZOWbVafSC+P8YOa3+OIJtc5DSgbg5kJba3Yvn2D+zfYLlTx9wHv6O1uMHd7uK+BqUYUCbNbj9UN+uSKAOK24xSa5V8pwnw7/XXVfJV+O/HgFauJAYPfvRH/rKp/Jz1QBZ+TGZDFDq3QrRRzEPB/k/ToeHlHusD68o8SQKIOJqHmztkUIspKefOOOk/hnrbupogSMpqgyrX9KCg2pWVQ1YXkwoCZnKtGHJCUIb7edkvdI9/I9Gc54frwO3fNCHEq/Gfx4w2YASWXHvT8jIAiepNbV6bkMozb701thIWcmuc1t+b+7XJaCGrMAclGRl46QMPTZtbmue/jT89bE+8Mf4cD8j5uhU7RlbbRNJi4BlnHv9rvlVNTgPq2ysO+T5cJl1je0CqyNk2iIVw25L2ZgV9ua9DKQbUWkwRaNclUQbUpR/DV6fffu4cGRTayr5VEADgM2QhdWRxrzUFdWAAfVGoFBawcp7qiol0w0jX27IyjKHetq4mLDdJpXqA1KBgzy1kn49gE77b0AMOBgFG0fqslTiejdWkC9fsy8F1xfmOGDsX9vB89U95PnDRNsE9brWtC8PpTlyYzLr3rU8YMyKHXVj9XnSFf3+Ua27DLfmGcDtvfaP5/iBQJ+d9ntOA+rY0tiXc89ZBFYiDuNsgmMd6Jq17GdzXoRQDykH8bj8p++IxHBIGNJbrp4zde0KEyLcxZ97YkOxKv7m/fcOaoIWmA58ZVENxb3Iexhjqbetqgnwyqw0r8tgAg1ysXL07+BBtJhl8bzzk481vR+4X6zMiBqCmCR21gnG3Wm0rtZV2nPG8f0umbaDElW+1q9RmxHwrnEq4T5sGPwy4z/tAtZ+me9FXwzsm/iAXOQ2oL9o5JbDPV5GIlXsbbnAjYjvFh/talGJArSISXR+S/4E0oOSPWe+Hi6YN394AbjE3CtKHzwghBtUQeC93o59BKYZ627qa8O05E4wxnpDfG1O4mxUpe7bjZfTBd9+jEDehNVBVOvbUuWUkbxNcu+8ggBBjYrVDIbnATA6stpVCAvvY37Laoibjy1aD1SZm8pqLnAbUF5vQ9ltY+LwjuNGbYJXptmFy2xSL4L4epRhQApzcfrqOyP9AGlD2NKz3a4tixRVitUNLXrbdExbs3VkJzyjkmjGeVgCKz0Xiw21fqQnfb4VrerxhoCC/1zeQWOLgA+t0ikHg+y4ZcEJOMyJH0mqPQgvq+yZE7Ke1YbVDoZG8FFS32uO6DpmMsgpmImT10RQ4w8lAVhtfkGOX5DSgVj8oZZJ4/+/jx2SeP+tYw7aTkdzXoxQDCq5rn/sDD1VXfCANKAEC1vuRKN2EFeWFMLyxN+mPfmqX3PJdMwMKqxL28aybNLaMH7h9VGrCVwGIQW+iwD4Wbvq26OtKDOTj4dL13ffcGyGw6rbao9AzHH2rsZDf02qHQiPa3TSsSjEVtS681C471+SCZg/TaoOowjNIchpQX9pSzNGSFd4VaMOKzjoFhtq0bWOj2walGlA8D9y79b4IHMW7yGQxNIo4lEPWgPJFUl2ElRqrjONPn1u6GZuiZ1ETnEhgtYk9fQYIfLL68l0zszvr9axWSHtImWVa/aEmrI161Db5GA/wNOASD9kfJX2kydVFdDe/TayaKvzwd+uzWKH+Fr6JIAqtxkTlIKt9yCkWVjsUWl7P9wyEbmOAL9ilba/uWxfaucyIil5twUS5yGlAfWNbPaI4FF9Oqe97xSXven74/5DAzHqbSqkGFPjtyHqwJhT99GtxSBlQSvMxy/C5hkLUhC/8n1qZscRes2VACTShtmnTwN+E21+lJkjJsdogK9pzIkCpRarstCX3NwXd+Aa6NjXdw/3e90yarPYoFN/EDLVhtUGh9Hv94FsptfVBdK/VrhLeC/aBSVnrkpwG1HeMWUwd3ArKP1p9WUXpuQ+t3F1qLofgtkP9Gjo8MPSRu1+XQ8KA4t4kgrap3meomiC6z2rDnkossdfcNNDhQq5KqMVg9YWasIIEKpFrO5EhyOCb3/WvPBg0fZVWJqIBBas9isFqj9qw2qBQclx/P32EptNQn7qr4/lyGlBfjm2oO7+Oz73OvruLVWCHILbQib3bFvVj6LAFvnz/2AM32hh6A8p+BrUVrfYpasLnIglxU7ikXDOuMfLQCDF3UxiIfIwtqF1vX1cTvhqoiOpMEx32gzihwfr8yFc7UwZ0LFYbFEqO6++nD1ZOBMv49g5dMfhSozcnOQ2ozy2dYvwpKWn15e4hkpPrFs9A1DHmNwiR2xaxpeK+LiRQ0zpkgpgRjDzpSyHBaTEMtQHFYDTVzGRfjv0MqmIsG/nhycEkJ4pBNOXGtV6P6DeWfr87KwKT/ckY3PaVmuAGdA/GrTQeeXQp4Gr+wnH27+87P5DBiXsmVuyd+uj3HgCrPYrBao/asNqgUHJcf44+8KpYhRUsMRjnTM7nHrHeJwWrihMKSQlyYQVp9eUWZfAdbN+F2tKMSNtyT+Pi9+oyyn6oDeiNt9gBBCzf+bKbZospN64vPYKk9lhyfHfuKRKUcYuh3rauNqwi+Ijk92E5SowcUOsaWNnnnqX6yHEPWO1RDFZ71IbVBoWS4/pz9AHctxQetyLcXfGaiVhM3vddEB0bA/e/NdZRucp9Nppy2nOrzYBa6UldHyoxtAYUv75Vko9/CykgnHLj+vZAFyac1J6SZ+Vym5MLiislhnrbutrw5Q4ia49kIoLXwPr8yHc+ZW5yPD9WexSD1R61YbVBoeS4/hx91MGtSw5p27YQdbVzkNOAzvMUlsCdGoOv3jVBlC4TyYBanyX2kJBYhtaA+qLvQupgQsqNS1Frq01IeSsXX6msmO+O0oH1tqy8Y6i3rauNpn1QXKApKTWDpqkUXcyRTf2Q4/mx2qMYrPaoDasNCiXH9efowwdF5X11lknzybEKzWlAmfhZfRGdG/NM+iLtrUnDRDKgBA+5bVK212IYWgPqSymhYHsIKTcuxtlqQ55pLJxsb/UV8925oea4H2Oot60rBF9JQzQMZ3Gyf259dkRgxCDI8fxY7VEMVnvUhtUGhZLj+nP00QQnmbin41RixdcvOQ0o+PYuQ8dF8JWItA4R5zliwtmPrPe6avLSMa9rC+CytmU4ZLtLhtaA+maGoUnDHHNltW+CI42sNhiuHS2nV9Rhs9uXsxXz3bkFudmDjKHetq4Qmk5lIZ0o9HSc8cJXzo37alDkeH6s9igGqz1qw2qDQslx/Tn6aMMXa/Hgo3FBexa5Dah1RB4KPeWJnGkrHZAMhK6OBHTfC6WksWDg3X5iy5vGMrQG1Bd6HpJ71FTIuglmQL5UlpiDsCm8YPWBYr47ymTV23IOZAz1tnWFgEvonAv8+0TUxu3afdIPN3m8CT+4It9hyW3keH6s9igGqz1qw2qDQslx/Tn6aMMXadpU1i6U3AaUlabVH9W4QgqdEEhltaeyT1dY75diQDn70+0nJQI5hqE1oL5UCvIk28DYWW1RG74EY4KXQmY71Fz1BSOhmO/OTZym3xjqbesKhSotTfVmWRGnnIYfSkoBC1i6bKc30XqQ7uccz4/VHsVgtUdtWG1QKDmuP0cfbbDStN4j5GzMNnIbUPAdrM1h6k2wQPCNTV2u5Kz3SzGgnGHr9kPAY5cMrQE95Rw7/5PI1CY4ysw3eKK2FAaiunwHclMqbv4Cv8Eg+KatzGDMd+fWeOUA4hjqbeuKgTq8Vh91XT5pSbFmbdxeBJGATW2qgAlW4ZzRGlIwm1UzM1JfST9qJePCGhQ5nh+rPYrBao/asNqgUHJcf2ofbDGEBNY0eVpynPLRhQH1ndLDuOWb0LKtRLSu1Q6DHBOEFIv1nikGlLHbHdtvvyu+TnkMQ2tAfYWo+QI5WNWFL5cZoy8goFKIC5hoNKttJdyAuGnJDyXdZtGL28ui123vjWK+O3evwgozb6Letq4YeLBuuNkusu+KyQN7MUQ34m5hQkFwAMaS2qS4yqbcvqo47rSDK2uK9/twD4NmT5tTTFgtMEmiT4pK8/1TwQR324meA5grWXU+uyTH82O1RzFY7VEbVhsUSo7rT+mDe/aIo2eVk3Aq1/gS7ZlM+Vz9bJe0TbZD6MKAcn1nn28HWeIxoi50tZ/Ja5kINJW47KqMYYX1nqml/Phd6v1MujbujORYhtaAMjA2rSQvuHhxeZgqxdaZhRx1YlilkZB9Akrq+Q4iDtWZ59k3eOh3x43vroRDj8GqqLetKxYGEo5Ts/rqRxhcH9feNLZQdD+6cvLS8jsdJDmeH6s9isFqj9qw2qBQclx/Sh94NuqvZRxh8kmwEEUHSJeggpkvUBER8ZmDLgwoMIGk8IHVN+KaqcblC6asxIS2a6z3TTWgZ5w72n2Nh6pLhtaAgltIIFTcNL5jkELPhSTqtlopxYo9WF8xAmaHITA7dttyTTG47SulwlmKMYdZt4lAMUovumDo3JlmP7ps0pLgwtc5yfH8WO1RDFZ71IbVBoWS4/pT+rDOrYwRxeVzrD6hKwMKeOJ8200hYhGScpZoLNZ7pxpQt871MSfP6f2lG4bagPLj+g7U9Yl9LlwWCxbZaRjM3ELh+LRLr15i9mOJWR8PLwbAZ0BDN70x4G7bmHMUwW1fqR/4/nyl/lL00tKxwQt8702rg1DhzuIeyzUYxpLj+bHaoxis9qgNqw0KJcf1p/TRj/eInO+cx/Z1aUCB7ZKQrSNXjGsp54imYL1/qgF1gzyJd+iSoTaggBFlJdrkzq1E8QIq8gMDvfUa9itjISey6YBe8kQJpKkn9foM6LQnNvde0QzX4bYNzfWqcNtXygH7JrhFU1ekzJyZ6fvOY8SIPjByf/gGoCbh2sIFnHLMU05yPD9WexSD1R61YbVBoeS4/pQ+MCqxRpToVFI8crv5uzagQOBj6IlVLDC6uM4mrM+RakAZc+r9YBe6pC8DyiDJjeoqdtM5Rz8EpLB3wV4G0anMuqgNy+Y4Je/clSWzK+s9+znTklUhEaFEpjK449JcsHi7GaTgK0VoBUBZWJV0Lrkyrualdf0oJ7hg+U7Yh8ZbwKkXBD9VriUmF/xOJ501v5z13n3v2vL1GMgQeNBJXXp42qZy9klgCOkz1YQKA467lwGE/ZyZc7Z2lhAeS4773mqPYrDaozasNiiUHNffTx9Mzij/xn1Hgfhqz5CtA+4h9tPYFiGyvitXJqf1WJ+/C/hOeAZ41qprZZzk2tnzJUJ9UKvOOtb1N2UzNHGCEyhIwZou6cuAinSIDqv/0JVWRYTGuzlbPBScjyqEEB80WGnXx0NEClKXyICOE5brhplvzP7K5OvHFnXgINyJssISQohBgPfPOhvad0B+LmRAxwH2Qt0fGpGnGAOHhFv9HHbkc+UKF9c17lAhhDjUeOzJzWV1JaLorZQdtodyHn5uIQM6DpCv6f7YiOIQsfhOoa/EyQpCCHGo0ZZGeO/UblefIAM6YNiot35sROWiWAhuuOZGf1EBGVAhxKGIz4CyFcbKdBCRxDKgiVAyjvM4if4NgVzDh6Zt9KbbpJwpWocC6Rxv5tbHlQEVQhyKuAaUoMrrp6zoK5MiFhnQROp5n6TO3Dd1fbFw8fbS506VIIozE8zDgbwYzqYi8iT0p6w+LZh1UU2J/las2lVs2jKxz+UUQogUKMlIURxSFHe/OT7ZBzKgCZDXGVK4IVS56moKIYQYHDKgCVDJxDKEKaLgghBCiOFDBjQBcossYxgj/PXzXlCKiRBCDCsyoIlwQjvlrz50uH04s0/Hnjq3DEAa5MHNQggh8iMD2icH3n2/WLlqd1kE/tY7VxdXTV5a1nw9/6JF5X8paECR96dnvDruxcuFEELkQwZUCCGESEAGVAghhEhABlQIIYRIQAZUCCGESEAGVAghhEhABlQIIYRIQAZUCCGESEAGVAghhEhABlQIIYRIQAZUCCGESEAGVAghhEhABlQIIYRIQAZUCCGESEAGVAghhIimKP4XBcAIzFfvoBoAAAAASUVORK5CYII=" |
简单流量分析
流量分析题,分析的方法基本上有:binwalk、查找一些可疑字符串或16进制数据,排序流量包的长度(最长的流量包一般很可疑);当我们对流量包的长度进行排序时,发现流量包最短90字节,最长也不过164字节,其中的data段数据长度从48到122,而ascii表中第48至122个字符为0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[]^_`abcdefghijklmnopqrstuvwxyz,于是将每个流量包的长度转换为对应字符,然后连接成一段长字符串,看上去像base64编码,对字符串进行base64解码即可!
1 | tcpdump -r 1.pcap | awk -F ' ' '{print $14}' > 1.txt |
1 | #!/usr/bin/python |
这段代码使用了 pyshark 库来读取一个名为 fetus_pcap.pcap 的数据包捕获文件。pyshark 是一个基于 tshark 的 Python 数据包分析库,它提供了一种简单的方法来解析和分析捕获文件和实时数据包。这个库可以用于网络分析,协议分析等领域。
这个脚本首先创建了一个空列表 L_flag 来存储数据包中 ICMP 层的 data_len 值,然后利用 pyshark.FileCapture() 函数读取指定的数据包捕获文件。之后,它遍历每个捕获到的数据包,遍历每个数据包的每个协议层。如果发现一个数据包包含 ICMP 层且其类型不是 0,则将该数据包的 data_len 值添加到 L_flag 列表中。
在此之后,代码将列表 L_flag 中的整数转换为相应的 ASCII 字符。最后,它将字符列表传递给 base64.b64decode() 函数,以解码 Base64 编码的字符串,并打印解码后的结果。
工控安全取证
下载后是一个capture.log,考虑到都是流量,改成wireshark能识别的后缀,capture.pcapng
打开后发现大量的tcp流量,不难发现,192.168.0.99是靶机,使劲被人攻击。
开始我的策略是手工分析出四个攻击时段的节点,于是就将时间显示格式调整为比较友好的类型,如图:

想以时间来区分,后来发现图样图森破,时间都很接近,那么多tcp怎么搞。
于是想到了协议
在进行一次连续的tcp之前一般会发一个icmp包过去,把过滤协议设置为icmp
,排序后,发现ICMP协议貌似刚好分成了四段(去掉了不成功的),如下:

ICMP请求第一组编号有发出也有回显正常的信息,我们认为该次扫描为一次正常的扫描;第二组和第三组同理!!!
第四组为什么是155989?第四次我们可以推测在155987到155990之间。
flag{155989}
fanfie
参考文章:https://blog.csdn.net/l8947943/article/details/123397127
1. 找到加密信息
题目给出的是一个txt文件,如下字符:
1 | MZYVMIWLGBL7CIJOGJQVOA3IN5BLYC3NHI |
这个题目最难的是缺少提示,看到都懵了,原题提示有如下:
任务描述告诉我们标志被转换为base32并以某种方式加密。
假设明文是这样的:BITSCTF{},那我们尝试将BITSCTF*进行加密,代码如下:
1 | from base64 import b32encode |
加密结果如下:
1 | IJEVIU2DKRDA==== |
对比原始字符,我们选取前一段的:
1 | MZYVMIWLGBL7CIJO |
可以看到M对应I,而且出现了两次,那么我们推测可能是一种单字母替换密码
找到映射关系
我们构造一个简单的字母序表:
1 | A B C D E F G H I J K L M N O P Q R S T U V W X Y Z 2 3 4 5 6 7 |
可以发现原始字符和base32加密后的对应索引关系:
| 映射 | 编号 |
|---|---|
| M -> I | 12 -> 8 |
| Z -> J | 25 -> 9 |
| Y -> E | 24 -> 4 |
| V -> V | 21 -> 21 |
| I -> U | 8 -> 20 |
| W -> 2 | 22 -> 26 |

什么是仿射密码?参考链接
举例第一列,A在原始字母表中的顺序为0,带入函数(13 * 0 + 4) mod 32 = 4,在原始字母表中,对应字母E,因此原始字符则有如下对应:
1 | MZYVMIWLGBL7CIJOGJQVOA3IN5BLYC3NHI IJEVIU2DKRDHWUZSKZ4VSMTUN5RDEWTNPU |
1 | from base64 import b32decode |
simpleRSA
求E1
由q = next_prime(getPrime(16) * p + 38219)可知,q为p*getPrime(16)+38219的下一个素数,因此getPrime(16)较小,所以我们可以在其取值范围为遍历出符合题目的值,从而解出q。
1 | for i in range(2 ** 15, 2 ** 16): |
做到E2就麻了,Crypto先做其他简单的题吧
onetimepad
Crypto先到这里吧
cr2-many-time-secrets
尝试了几个编码不行
题目中提示是One Time Pad的重用导致的攻击。
一次性密码本 one-time pad(OTP):
key的长度大于等于messagekey必须是一次性的,且每次都要随机产生
满足上述两个条件,即称为 OTP
异或加密特性
- 两个值相同时,返回flase,否则返回true
- 如果对一个值连续做两次XOR,会返回这个值本身.
- 假设原始信息是
message,密钥是key,第一次 XOR 会得到加密文本cipherText。对方拿到以后,再用key做一次 XOR 运算,就会还原得到message。
加密101-异或(xor)
工具
https://github.com/SpiderLabs/cribdrag
简单来说呢,就是利用一些用同个密钥生成的密文,猜对其中部分密文对应的明文,即可求出公共密钥,再用该可能的密钥去解其他的密文,若符合,则为密钥正确。
1 | python cribdrag.py 0529242a631234122d2b36697f13272c207f2021283a6b0c79082f28202a302029142c653f3c7f2a2636273e3f2d653e25217908322921780c3a235b3c2c3f207f372e21733a3a2b37263b3130122f6c363b2b312b1e64651b6537222e37377f2020242b6b2c2d5d283f652c2b31661426292b653a292c372a2f20212a316b283c0929232178373c270f682c216532263b2d3632353c2c3c2a293504613c37373531285b3c2a72273a67212a277f373a243c20203d5d243a202a633d205b3c2d3765342236653a2c7423202f3f652a182239373d6f740a1e3c651f207f2c212a247f3d2e65262430791c263e203d63232f0f20653f207f332065262c31683137223679182f2f372133202f142665212637222220733e383f2426386b |
历时3个小时终于把这个脚本或者说python2的环境有搞好了.
若是明文中的则是message
若是flag则为key

ALEXCTF{是key
一点一点猜测下面的内容
Decode_The_File
找到了python2的脚本改一下
1 | import base64 |
streamgame1
1 | # flag的长度为25字节,25-6=19个字节 |
题目给的很详细了,但是现在确实做不出来,但总不能不做了吧,看WP
那么我们的任务很明确,就是通过分析lfsr函数,整理成数学表达式的形式求解即可,接下来我们对代码进行逐行解读
1 | def lfsr(R,mask): |
通过上面的分析,我们可以看出在这道题的情境下,lfsr函数本质上就是一个输入R输出lastbit的函数,虽然我们现在已经清楚了R是如何经过一系列运算得到lastbit的,但是我们前面的反馈函数都是数学表达式的形式,我们能否将上述过程整理成一个表达式的形式呢?这就需要我们再进一步进行分析:
1 | mask = 0b1010011000100011100 |
将其写成数学表示式的形式,即为:
lastbit=R3^R5^R8^R9^R13^R17^R18^R19
显然lastbit和R之间满足线性关系,那么接下来我们就可以开始求解了
关键就在于这个key如何去解,一开始我是之间复制粘贴,取前19位,发现全都是0,后来直接看了一下key的全部值,发现在最后几位才出现1.
1 | import os,sys |
正确的是这个脚本
https://blog.csdn.net/xiao__1bai/article/details/120399710
1 | xiao__1bai师傅: |
1 | f = open('5key','rb') #以二进制格式打开文件 |
这里说的lastbit就是key的值(这里是之前一道题的图,也是跟着之前的思路做的)
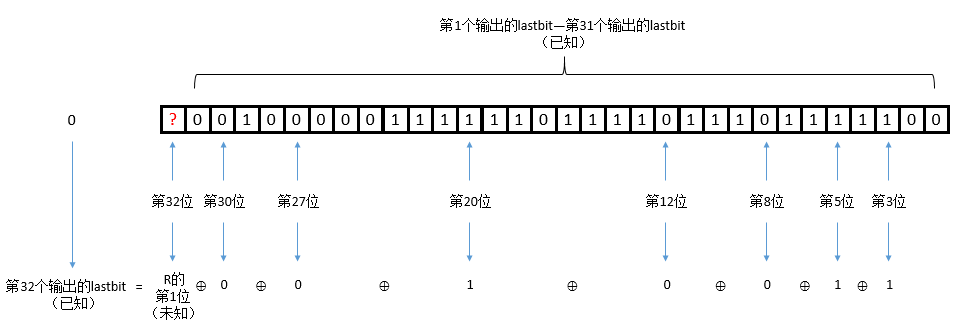
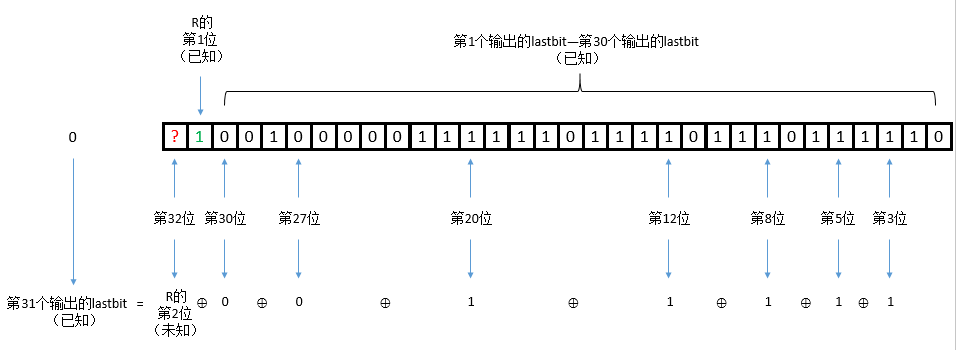
这样我们就可以求出R的第1位,同样的方法,我们可以求出R的第2位:
1 | # 开发时间:2023/3/14 11:38 |
Normal_RSA
确实是普通的RSA
1 | # 开发时间:2023/3/12 15:01 |
easy_ECC
椭圆曲线加密算法

要调整为10进制
点CALC R
说我作弊需要证据
追踪数据流我们注意到从Alice(192.168.0.13)和Bob(192.168.0.37)的每个数据包都包含base64编码的有效负载。
看时间猜测是A给B发
解码几行
1 | SEQ = 13; DATA = 0x3b04b26a0adada2f67326bb0c5d6L; SIG = 0x2e5ab24f9dc21df406a87de0b3b4L; |
实在搞不出来了.按着风二西师傅的wp做的,我只能说yyds
1 | import libnum |
第一部分不再赘述
看这个
1 | with open("1.txt","r") as f: |
find() 是 Python 字符串对象的方法之一,用于在一个字符串中查找子字符串,并返回第一次出现的位置
Easy_Crypto
1 | get buf unsign s[256] |
前半部分是RC4
主要看这里
1 | for m:0 to 37 |
加密操作是异或,而我们又知道他加密的全部过程,所以再次用相同的步骤异或一次就可以得到明文
根据伪码逆着来
1 | key = 'hello world' |
Easy-one
加密代码
1 | #include <stdlib.h> |
1 | char k[] = "CENSORED"; // 初始化一个密钥字符串,但真正的密钥不是它 |
在循环中,每次读取一个字符 p,然后计算出一个加密后的字符 c。加密过程中,首先从密钥字符串中取出一个字节进行异或运算,然后加上上一个字符 t 和计数器 i 的平方。最后将结果与 0xff 做与运算(这是一个二进制掩码,用于确保加密后的字符只有一个字节),并将结果赋值给加密后的字符 c。
然后将当前字符 p 保存到临时变量 t 中,以备下一次加密使用。计数器 i 也会递增,以便在下一次循环中使用下一个密钥字节。最后,将加密后的字符 c 写入输出流中。
总体来说,这段代码使用简单的加密算法将输入流中的数据加密,并将加密后的数据写入输出流中。密钥字符串可以根据需要更改,以生成不同的加密输出。
1 | f1=open("msg001",'rb+') |
接下来解密
1 | f = open('msg002.enc','rb').read() |
x_xor_md5
放入HEX后就没思路了,
01780C4C109E3237120CFBBACB8F6A53
WP上说:怀疑 重复的内容就是 xor key
用 xor key 去和每一行的数据进行 异或运算,
再将其 转为字符:
1 | # -*- coding:utf-8 -*- |
得到有ctf字样的乱码,说明思路没有出错,还需要进一步操作

审查得到的 16 进制列表数据,发现 不应该出现0x00,0x00是绝对意义上的空,而空格 是 0x20
所以猜测应该是 所有数据还要和 0x20 进行 异或运算
1 | def file_xor_20(*n):#16 进制数组 XOR 0x20 |

这里只需要跟假key异或即可,并得到疑似的key=21582c6c30be1217322cdb9aebaf4a73
疑似的 flag 为 RCTF{We1l_d0n3_ut_wh4t_i5_key },但 FLAG 中最后一列的字符还有非可显示 字符(key 后面是个空格,还有 ut 前面,并且这两个位置都是每次key循环完成后的第16位),说明最后一列的KEY不正确,猜测 key 被两个包括,即key*,所以就是 0x00^0x2a,尝试调整后得到真正的 key: 21582c6c30be1217322cdb9aebaf4a59
1 | def getkey(): |
1 | for ii in range(11,99): |
也可以爆破一下
