Crypto-AES题目
Crypto-AES
参考文章:http://f0und.icu/article/27.html
https://blog.csdn.net/qq_51999772/article/details/124301715
单独涉及AES_ECB模式
最常见的是RSA中套了一个简单的AES_ECB加密(AES加密flag),RSA加密的是AES_ECB模式的密钥key,解RSA得到密钥key进而求得flag
单独涉及AES_CBC模式
(陇原战疫2021网络安全大赛 Civet cat for Prince)
keywords: AES_CBC,xor,狸猫换太子
1 | #题目.py |
[安洵杯 2020]easyaes
1 | #!/usr/bin/python |
明文都是先于混淆数据(第一组是于IV,之后都是与前一组的密文)进行异或,在执行分组加密的
加密:
1, 首先将明文分组(AES128以16字节为一组),位数不足的使用特殊字符填充.
2, 生成一个随机的初始化向量IV和一个密钥.
1 | iv = flag.strip(b'd0g3{').strip(b'}')#删去头尾指定的字符串 |
3, 将IV和第一组明文异或
4, 用密钥对3中的xor后产生的密文加密
5, 用4中产生的密文对第二组明文进行xor操作
6, 用密钥对5中产生的密文加密
7,重复4-6
1 | aes = AES.new(key,AES.MODE_CBC,iv)#4-7 |
8, 将IV和加密后的密文拼接在一起,得到最终的密文.
解密:

每组解密时,先进行分组加密算法的解密,然后与前一组的密文进行异或才是最初的明文
对于第一组则是与IV进行异或
1 | def decry(key, IV, ms): |
1, 从密文中提取IV,然后将密文分组
2, 使用密钥对第一组的密文解密,然后和IV进行xor得到明文
3, 使用密钥对第二组密文解密,然后和2中的密文xor的到明文
4, 重复2-3,直到最后一组密文
根据这个加密流程我们可以得到
1 | 假设aes 加密函数为enc(msg,key),初始向量为iv,key = key, 则其加密流程大致为: |
而由于题目中所给出的hint长度与key长度不一样,导致我们可以推出hint,从而恢复出key
1 | tmp = 56631233292325412205528754798133970783633216936302049893130220461139160682777 |
而此时我们已经有的信息包括
1 | key |
我们要通过这些已知量求出初始向量
解密图: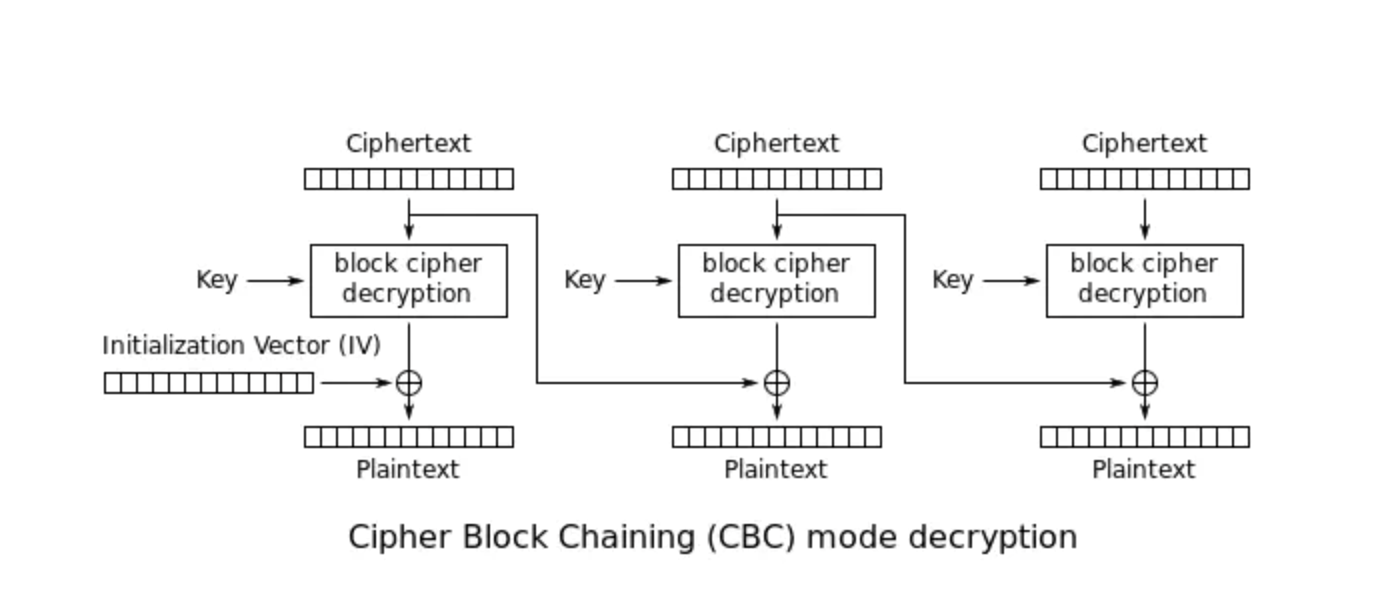
1 | 假设aes 解密函数为decrypt(enc,key),初始向量为iv,key = key, 则其解密流程大致为: |
所以就有
1 | def decry(key, IV, ms): |
1 | from Crypto.Util.number import long_to_bytes |
[SWPUCTF 2022 新生赛]AES
1 | #timu.py |
1 | #decry.py |
[SWPUCTF 2022 新生赛]Caesar?Ceaasr!
栅栏密码加密后出现类似flag格式…

然后就是移位
[HNCTF 2022 WEEK3]AES
1 | from Crypto.Cipher import AES |
[CISCN 2021初赛]oddaes(未解决)
1 | #chall.py |
1 | #out |
参考文章:https://www.tr0jan.top/archives/107/
chall调用了aes,常规CBC加密模式,只有密文和进行了部分混淆的密文,给了key的序列验证md5值,aes是正常的AES,GitHub上工具爆破得到可能的key。
[GWCTF 2019]aes(未解决)
1 | import hashlib |
[安洵杯 2019]This_is_not_a_standard_AES256(未解决)
nc 获取信息
1 | This is you Sbox(tuple) |
[EIS 2019]aes
1 | b'(\xf1\xa9\x0f!\x9b\x98`\xc6-\x1b\xb6?C3M\xa8M-\x9b\xf9y<E\x93\x9a\x18\x86\xc4\x01\xf0p\xa4\xe7(:\x1aaP\xb9\xd3\xf1_b\x88' |
qsnctf-crypto-aes
1 | from Cryptodome.Cipher import AES |
bits和bytes都是计算机存储数据的单位,但是它们的表示方式和含义不同。
bit(比特)是二进制位的简称,表示信息的最小单位,通常用 0 和 1 来表示。byte(字节)是计算机中数据的基本单位,通常由8个二进制位(即8个bit)组成,可以表示 256 种不同的状态。
在Python中,bytes是一种不可变的序列类型,它表示二进制数据,由一个或多个byte组成。而bits则可以使用 int 或 bool 类型来表示,通常使用位运算操作来处理二进制数据。需要注意的是,在Python中,一个字节可以用一个整数来表示,如 0x1A 表示一个字节,而一个整数默认使用4个字节(即32个bit)来表示。
1 | #python3 |
